Malicious actors can exploit an endless number of vulnerabilities. No matter which or how many security tools have been implemented within the organization, the reality is new threats arise every day.
The U.S. government’s National Vulnerability Database (NVD) which is fed by the Common Vulnerabilities and Exposures (CVE) list currently has over 120,000 new entries in 2022 alone.
Teams cannot just assume they are covered. They need to be able to determine what vulnerabilities exist and the level of risk of exploitation. And if there is a gap in coverage, how should it be addressed to reduce the likelihood of attack.
Attackers are getting faster. That’s a problem for organizations trying to keep their networks protected. To make matters worse, Google’s Threat Analysis Group (TAG) and Project Zero have also observed an uptick in zero-day attacks, where attackers are exploiting a flaw before a vendor has released a patch for it.
Why Remediation Validation is Important
Vulnerability management is more than just scanning and detecting vulnerabilities. The ultimate goal of any program is to reduce the level of risk within your environment. Vulnerability management is a cyclical process that includes discovery, prioritization, remediation, and monitoring to ensure a successful, long-term fix.
How this is accomplished will be influenced by the cybersecurity framework that your organization has chosen to use. Often this is dictated by the type of operation that you run. Some of the well-known and popular frameworks include NIST, PCI DSS, and CMMC.
Testing the effectiveness of your security controls along with ongoing monitoring is critical to protecting your environment.
Remediation Validation helps security teams by:
- Ensuring that any security controls in place are actually working as required
- Discovering any additional security gaps, so they can be addressed before they can be exploited
- Identifying if misconfigurations may have occurred which may result in new threats and vulnerabilities
- Monitoring when issues are closed and gives insight into actions taken to reduce risk
Remediation vs. Mitigation
A common question that comes up is “what is the difference between remediation and mitigation”? While the terms are often used interchangeably, they are different.

Remediation is the process of eliminating detected vulnerabilities in your network. This is often accomplished through patching. Making yourself aware of the typical patch release schedule from relevant companies like Microsoft and VMware can help reduce your exposure to cyberattack. CISA also releases regular updates and keeps a catalog of Known Exploited Vulnerabilities.
But, there are instances in which patches are not feasible.
- The patch has not been released by the vendor. It takes time to prepare and distribute them so there may be some delay in patching.
- The patch may create additional problems across the network – or bring it down altogether
Mitigation, on the other hand, is more like damage control. The vulnerability cannot be eliminated immediately but it can be minimized. This is often a temporary solution or workaround to decrease the possibility of the vulnerability being exploited. Examples of mitigation include:
- Disabling the software temporarily
- Blocking a port on a firewall
- Removing unneeded or unexpected hardware
Additional mitigation strategies can be found in NSA’s Top Ten Cybersecurity Mitigation Strategies document.
How Often Should Remediation Occur
Many organizations have chosen to scan and patch on a monthly basis. While this may sound efficient, new vulnerabilities appear every day.
Industry reports estimate that adversaries are now able to exploit a vulnerability within 15 days (on average) of discovery. In fact, statistics show 60% of breach victims said they were breached due to an unpatched known vulnerability where the patch was not applied. An even higher portion (62%) claimed they weren’t aware of their organization’s vulnerabilities before a breach.
To ensure effective and timely remediation of vulnerabilities identified, organizations should undertake the following actions:
1. Scan the organization’s entire attack surface (IPs)
Prioritize and sort vulnerabilities. This includes creating and maintaining an asset inventory of all your IP addresses, including external, internal (datacenters, corporate HQ, satellite offices, etc.), and cloud IPs (AWS, Azure, Oracle, etc.)
2. Maintain an updated asset/target inventory
Include any newly acquired IPs or re-assigned IPs that are no longer part of your inventory. It’s common to have both static environments where assets do not change and dynamic environments where devices change IPs. Leverage both blackbox and whitebox asset identification methodologies.
3. Review scanning results daily/weekly/monthly and prioritize vulnerabilities that are found
With new vulnerabilities published by NVD daily and CISA regularly publishing alerts of known exploited vulnerabilities or nation state attacks, organizations should review their reported vulnerabilities at least on a monthly basis, preferably weekly or daily.
4. Remediate vulnerabilities
Prioritize and sort vulnerabilities in order to maximize risk reduction. CISA provides guidance around remediation timelines, but most organizations maintain their own internal SLA for how fast an issue should be remediated, based on acceptable risk.
CISA recommends the following remediation timelines:
- Critical vulnerabilities should be remediated within 15 calendar days of initial detection.
- High vulnerabilities should be remediated within 30 calendar days of initial detection.
- If vulnerabilities cannot be remediated within the recommended timeframes, develop a remediation plan for action and coordination across the organization. The remediation plan should include:
- Vulnerability remediation constraints
- Interim mitigation actions to overcome constraints
- Final actions required to remediate vulnerability
How Remediation Validation Works
VULNERA recognized the challenges faced by security teams. Corporate networks are constantly changing – devices and services connecting and disconnecting all day long. Distributed workforces, mobile devices, IoT, and cloud computing have all increased an organization’s attack surface. From chasing new assets and thousands of security alerts, security teams are overwhelmed.
Our Remediation Validation and Continuous Assessment solutions were built to overcome these challenges. After every scan of the target environment completes, an automated retest is conducted and remediation testing activities are tracked and updated, including the observed remediation reason. Remediation tracking helps answer the questions:
- Did the patch resolve the issue?
- How many issues were closed with the patch?
- How and why was the issue closed?
Each vulnerability has its own audit trail including what remediation actions were performed and when. The environment continues to be monitored for additional instances of the vulnerability. Additional instances may indicate that the root cause has not been addressed.
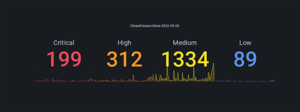
A dedicated dashboard highlights resolved issues accompanied with the remediation reason and confidence level. Additionally, new assets and vulnerabilities may be uncovered during follow-up security tests.
Remediation Validation helps organizations determine:
- Missing security controls
- Misconfigured controls
- Effective/Ineffective controls
Remediation Validation is an important component of a mature vulnerability management program. It may reveal that new processes or tools are needed to address certain shortfalls. Validation ensures that all the components of your security program are aligned, well -integrated and performing as expected.
You can learn more about how VULNERA’s solutions can help you on our Solution Comparison page, or by scheduling time to discuss your use case with one of our Vulnerability Management Experts.



